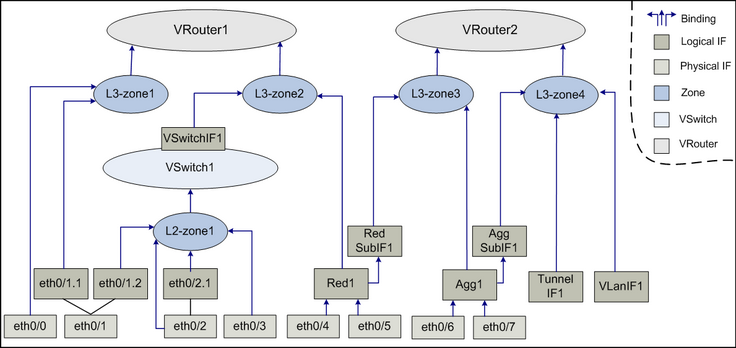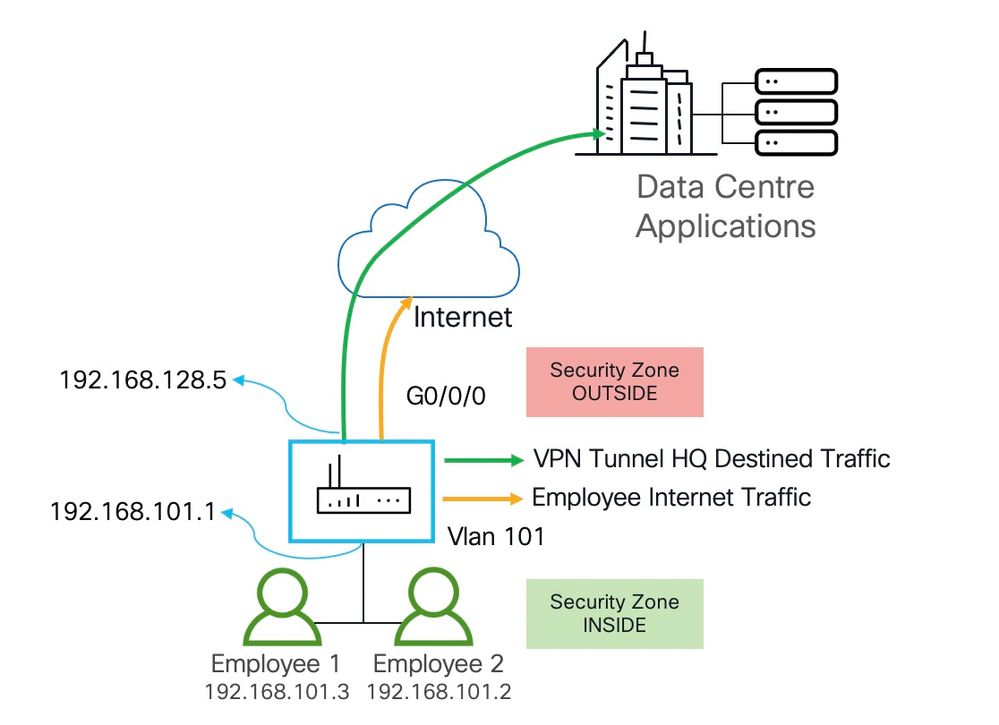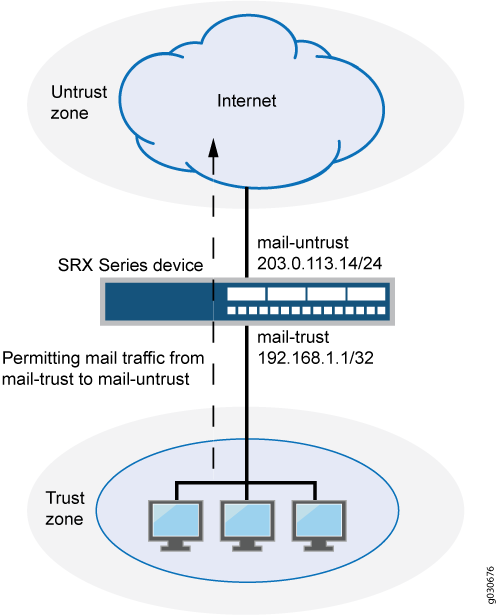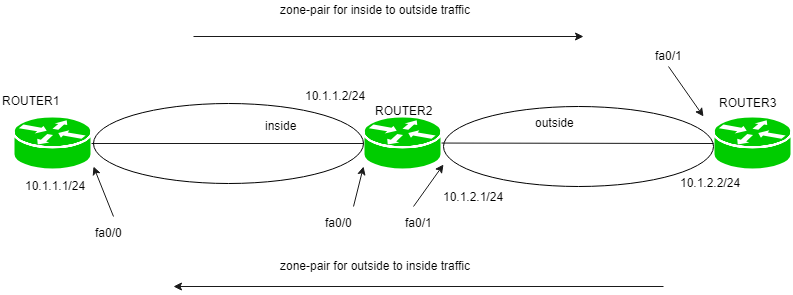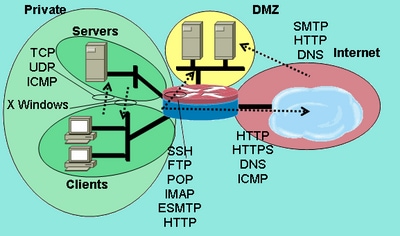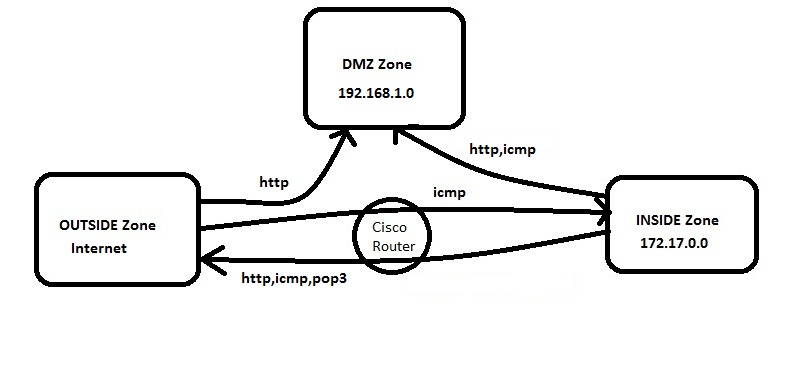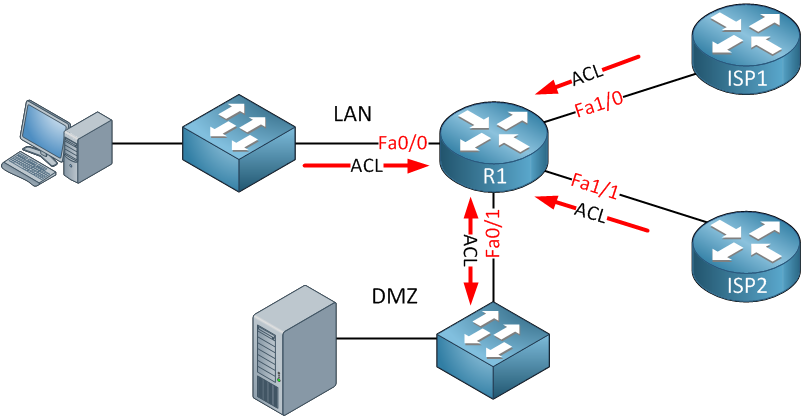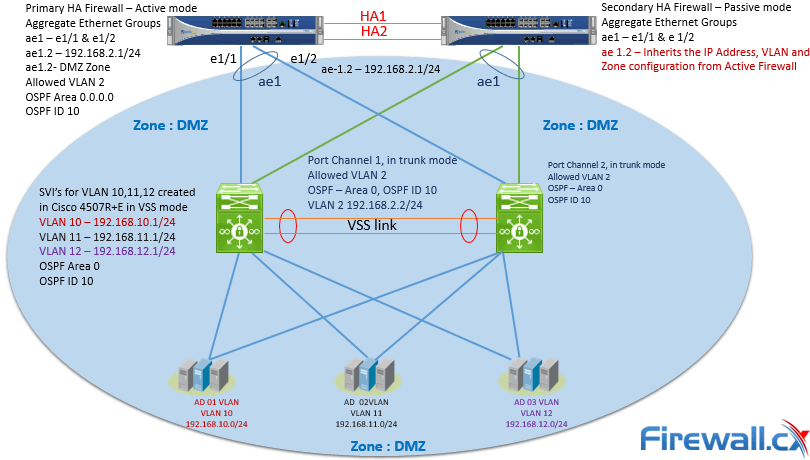
Security Zones in OpenShift worker nodes — Part III — Network Configuration | by Luis Javier Arizmendi Alonso | ITNEXT

Realtime Security zone - COFE Presenting The Most Awaited 4G WiFi Router With External Voice Landline Support Fast 4G LTE Speed Share Your fast 4G LTE Category4 Mobile Internet Anywhere anytime. Support